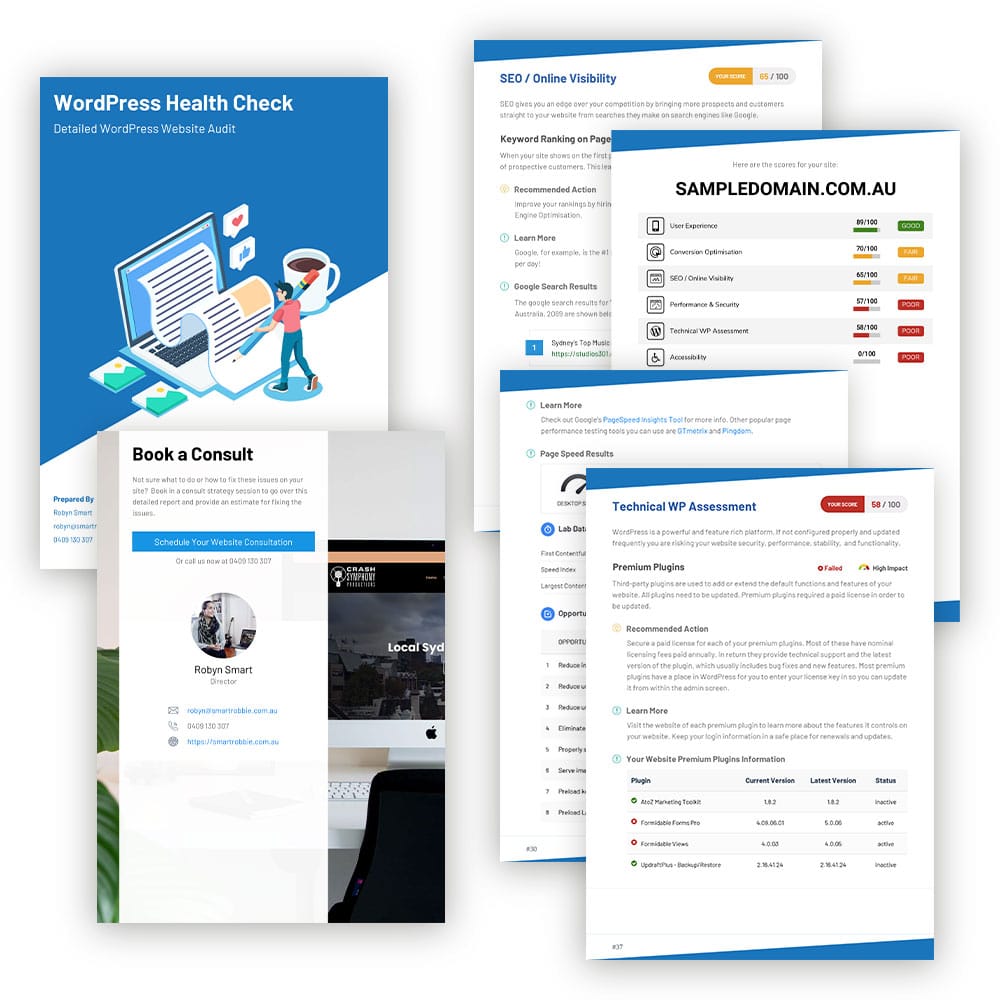
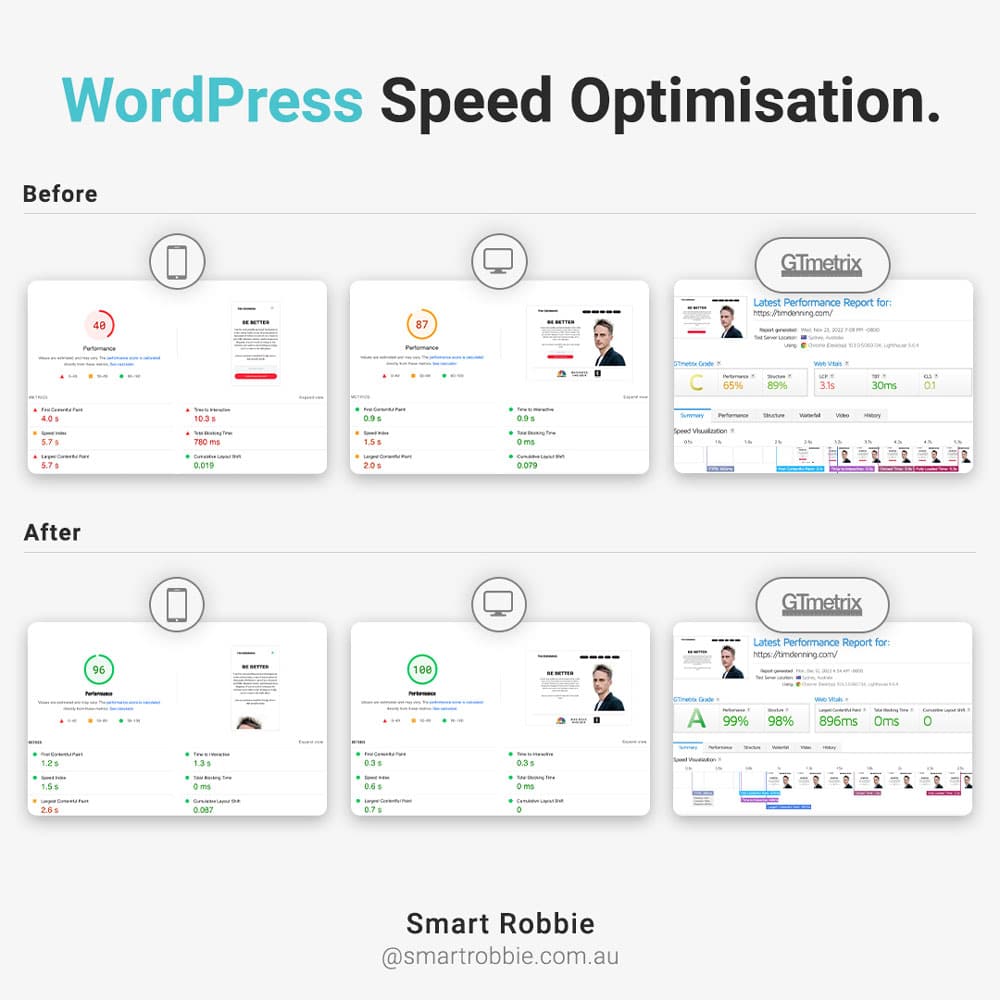
This WP Security Roundup shows the latest WordPress vulnerabilities including Yoast SEO, Easy Social Icons, Stripe Payments and more!
Plugin: Salient Core
Vulnerability: Cross Site Scripting (XSS) vulnerability
Vulnerability: Reflected Cross Site Scripting (XSS) vulnerability
Patched Version: 2.0.3
Recommended Action: Update the WordPress Salient Core plugin to the latest available version (at least 2.0.3).
Plugin: Yoast SEO
Vulnerability: Cross Site Scripting (XSS) vulnerability
Patched Version: 21.1
Recommended Action: Update the WordPress Yoast SEO plugin to the latest available version (at least 21.1).
Plugin: Booster for WooCommerce
Vulnerability: Authenticated Production Creation/Modification Vulnerability
Vulnerability: Auth. Arbitrary Order Information Disclosure Vulnerability
Patched Version: 7.1.2
Recommended Action: Update the WordPress Booster for WooCommerce plugin to the latest available version (at least 7.1.2).
Plugin: Community by PeepSo
Vulnerability: Reflected Cross Site Scripting (XSS) vulnerability
Patched Version: 6.2.7.0
Recommended Action: Update the WordPress Community by PeepSo plugin to the latest available version (at least 6.2.7.0).
Plugin: Captcha Code
Vulnerability: Captcha Bypass vulnerability
Patched Version: None
Recommended Action: No patched version is available.
Plugin: Availability Calendar
Vulnerability: Cross Site Request Forgery (CSRF) vulnerability
Patched Version: None
Recommended Action: No patched version is available.
Plugin: Simply Exclude
Vulnerability: Reflected Cross Site Scripting (XSS) vulnerability
Patched Version: None
Recommended Action: No patched version is available.
Plugin: WP ALL Export Pro
Vulnerability: Remote Code Execution via CSRF vulnerability
Patched Version: 1.8.6
Recommended Action: Update the WordPress WP ALL Export Pro plugin to the latest available version (at least 1.8.6).
Plugin: Export any WordPress data to XML/CSV
Vulnerability: Remote Code Execution via CSRF vulnerability
Vulnerability: Admin+ RCE vulnerability
Vulnerability: Auth. PHAR Deserialization via CSRF vulnerability
Patched Version: 1.4.1
Recommended Action: Update the WordPress Export any WordPress data to XML/CSV plugin to the latest available version (at least 1.4.1).
Plugin: WP ALL Export Pro
Vulnerability: Admin+ RCE vulnerability
Vulnerability: Auth. PHAR Deserialization via CSRF vulnerability
Patched Version: 1.8.6
Recommended Action: Update the WordPress WP ALL Export Pro plugin to the latest available version (at least 1.8.6).
Plugin: License Manager for WooCommerce
Vulnerability: SQL Injection vulnerability
Patched Version: 2.2.11
Recommended Action: Update the WordPress License Manager for WooCommerce plugin to the latest available version (at least 2.2.11).
Plugin: ChatBot
Vulnerability: SQL Injection vulnerability
Patched Version: 4.7.9
Recommended Action: Update the WordPress ChatBot plugin to the latest available version (at least 4.7.9).
Plugin: Easy Social Feed
Vulnerability: Broken Access Control vulnerability
Patched Version: 6.5.2
Recommended Action: Update the WordPress Easy Social Feed plugin to the latest available version (at least 6.5.2).
Plugin: Enfold
Vulnerability: Reflected Cross Site Scripting (XSS) vulnerability
Patched Version: 5.6.5
Recommended Action: Update the WordPress Enfold theme to the latest available version (at least 5.6.5).
Plugin: WP Roadmap
Vulnerability: Cross Site Scripting (XSS) vulnerability
Patched Version: 1.0.9
Recommended Action: Update the WordPress WP Roadmap plugin to the latest available version (at least 1.0.9).
Plugin: Porto Theme – Functionality
Vulnerability: Broken Access Control vulnerability
Vulnerability: Unauth. SQL Injection vulnerability
Patched Version: 2.12.1
Recommended Action: Update the WordPress Porto Theme – Functionality plugin to the latest available version (at least 2.12.1).
Plugin: TriPay Payment Gateway
Vulnerability: Cross Site Scripting (XSS) vulnerability
Patched Version: None
Recommended Action: No patched version is available.
Plugin: Frontier Post
Vulnerability: Cross Site Request Forgery (CSRF) vulnerability
Patched Version: None
Recommended Action: No patched version is available.
Plugin: Debug Log Manager
Vulnerability: Sensitive Data Exposure via Log File vulnerability
Patched Version: None
Recommended Action: No patched version is available.
Plugin: Easy Social Icons
Vulnerability: Cross Site Scripting (XSS) vulnerability
Patched Version: 3.2.5
Recommended Action: Update the WordPress Easy Social Icons plugin to the latest available version (at least 3.2.5).
Plugin: Hide login page
Vulnerability: Secret Login Page Location Disclosure on Multisites vulnerability
Patched Version: None
Recommended Action: No patched version is available. This plugin has been closed as of November 22, 2023 and is not available for download. This closure is temporary, pending a full review.
Plugin: League Table
Vulnerability: Cross Site Request Forgery (CSRF) vulnerability
Patched Version: None
Recommended Action: No patched version is available.
Plugin: Mail Bank – #1 Mail SMTP Plugin for WordPress
Vulnerability: Broken Access Control vulnerability
Patched Version: None
Recommended Action: No patched version is available.
Plugin: MyBookTable Bookstore
Vulnerability: Cross Site Request Forgery (CSRF) vulnerability
Patched Version: None
Recommended Action: No patched version is available.
Plugin: Bulk Comment Remove
Vulnerability: Cross Site Request Forgery (CSRF) vulnerability
Patched Version: None
Recommended Action: No patched version is available.
Plugin: Fast Custom Social Share by CodeBard
Vulnerability: Cross Site Scripting (XSS) vulnerability
Patched Version: None
Recommended Action: No patched version is available.
Plugin: NextGEN Gallery
Vulnerability: Cross Site Request Forgery (CSRF) vulnerability
Patched Version: 3.39
Recommended Action: Update the WordPress NextGEN Gallery plugin to the latest available version (at least 3.39).
Plugin: WC Vendors Marketplace
Vulnerability: SQL Injection vulnerability
Patched Version: 2.4.7.1
Recommended Action: Update the WordPress WC Vendors Marketplace plugin to the latest available version (at least 2.4.7.1).
Plugin: HUSKY – Products Filter for WooCommerce (formerly WOOF)
Vulnerability: Broken Access Control vulnerability
Patched Version: 1.3.4.3
Recommended Action: Update the WordPress HUSKY – Products Filter for WooCommerce (formerly WOOF) plugin to the latest available version (at least 1.3.4.3).
Plugin: Events Manager
Vulnerability: Reflected Cross Site Scripting (XSS) vulnerability
Patched Version: 6.4.6
Recommended Action: Update the WordPress Events Manager plugin to the latest available version (at least 6.4.6).
Plugin: Landing Page Builder
Vulnerability: Open Redirection vulnerability
Patched Version: 1.5.1.6
Recommended Action: Update the WordPress Landing Page Builder plugin to the latest available version (at least 1.5.1.6).
Plugin: Mollie Payments for WooCommerce
Vulnerability: Arbitrary File Upload vulnerability
Patched Version: 7.3.12
Recommended Action: Update the WordPress Mollie Payments for WooCommerce plugin to the latest available version (at least 7.3.12).
Plugin: Awesome Support
Vulnerability: Broken Access control vulnerability
Vulnerability: Cross Site Request Forgery (CSRF) vulnerability
Patched Version: 6.1.5
Recommended Action: Update the WordPress Awesome Support plugin to the latest available version (at least 6.1.5).
Plugin: eDoc Employee Job Application
Vulnerability: Reflected Cross Site Scripting (XSS) vulnerability
Patched Version: None
Recommended Action: No patched version is available.
Plugin: Accelerated Mobile Pages
Vulnerability: Cross Site Scripting (XSS) vulnerability
Patched Version: 1.0.89
Recommended Action: Update the WordPress Accelerated Mobile Pages plugin to the latest available version (at least 1.0.89).
Plugin: Video Player
Vulnerability: Cross Site Scripting (XSS) vulnerability
Patched Version: None
Recommended Action: No patched version is available.
Plugin: Salon booking system
Vulnerability: Editor+ Privilege Escalation vulnerability
Patched Version: 8.7
Recommended Action: Update the WordPress Salon booking system plugin to the latest available version (at least 8.7).
Plugin: Contact Form Email
Vulnerability: Captcha Bypass vulnerability
Patched Version: 1.3.42
Recommended Action: Update the WordPress Contact Form Email plugin to the latest available version (at least 1.3.42).
Plugin: Display Custom Post
Vulnerability: Cross Site Scripting (XSS) vulnerability
Patched Version: None
Recommended Action: No patched version is available.
Plugin: WordPress Job Board and Recruitment Plugin – JobWP
Vulnerability: Sensitive Data Exposure on Resume Files vulnerability
Patched Version: 2.2
Recommended Action: Update the WordPress WordPress Job Board and Recruitment Plugin – JobWP plugin to the latest available version (at least 2.2).
Plugin: Import Spreadsheets from Microsoft Excel
Vulnerability: Cross Site Scripting (XSS) vulnerability
Patched Version: 10.1.4
Recommended Action: Update the WordPress Import Spreadsheets from Microsoft Excel plugin to the latest available version (at least 10.1.4).
Plugin: Form Maker by 10Web
Vulnerability: Captcha Bypass Vulnerability vulnerability
Patched Version: 1.15.21
Recommended Action: Update the WordPress Form Maker by 10Web plugin to the latest available version (at least 1.15.21).
Plugin: TextMe SMS
Vulnerability: Broken Access Control vulnerability
Patched Version: None
Recommended Action: No patched version is available.
Plugin: Stripe Payments
Vulnerability: Broken Access Control vulnerability
Vulnerability: Content Injection vulnerability
Patched Version: 2.0.80
Recommended Action: Update the WordPress Stripe Payments plugin to the latest available version (at least 2.0.80).
Plugin: Decorator – WooCommerce Email Customizer
Vulnerability: Cross Site Request Forgery (CSRF) vulnerability
Patched Version: 1.2.8
Recommended Action: Update the WordPress Decorator – WooCommerce Email Customizer plugin to the latest available version (at least 1.2.8).
Plugin: Simple Testimonials Showcase
Vulnerability: Cross Site Request Forgery (CSRF) vulnerability
Patched Version: None
Recommended Action: No patched version is available.
Plugin: Taxonomy filter
Vulnerability: Cross Site Request Forgery (CSRF) vulnerability
Patched Version: None
Recommended Action: No patched version is available.
Plugin: Broken Link Checker for YouTube
Vulnerability: Cross Site Request Forgery (CSRF) vulnerability
Patched Version: None
Recommended Action: No patched version is available.
Plugin: Consensu.io
Vulnerability: Broken Access Control vulnerability
Patched Version: None
Recommended Action: No patched version is available. This plugin has been closed as of July 24, 2023 and is not available for download. Reason: Guideline Violation.
Plugin: Seraphinite Post .DOCX Source
Vulnerability: Cross Site Request Forgery (CSRF) vulnerability
Patched Version: None
Recommended Action: No patched version is available. No reply from the vendor.
Plugin: BackWPup
Vulnerability: Authenticated (Administrator+) Directory Traversal vulnerability
Patched Version: 4.0.2
Recommended Action: Update the WordPress BackWPup plugin to the latest available version (at least 4.0.2).
Plugin: EventPrime
Vulnerability: Authenticated(Contributor+) Stored Cross-Site Scripting via Shortcode vulnerability
Patched Version: 3.3.3
Recommended Action: Update the WordPress EventPrime plugin to the latest available version (at least 3.3.3).
Plugin: Quttera Web Malware Scanner
Vulnerability: Authenticated (Administrator+) Directory Traversal via ShowFile vulnerability
Vulnerability: Directory Listing to Sensitive Data Exposure vulnerability
Patched Version: 3.4.2.1
Recommended Action: Update the WordPress Quttera Web Malware Scanner plugin to the latest available version (at least 3.4.2.1).
Plugin: WordPress Team Members – GS Plugins
Vulnerability: Authenticated (Contributor+) Stored Cross-Site Scripting vulnerability
Patched Version: 2.2.4
Recommended Action: Update the WordPress WordPress Team Members – GS Plugins plugin to the latest available version (at least 2.2.4).
Plugin: Royal Elementor Addons
Vulnerability: Unauthenticated Arbitrary File Upload
Patched Version: None
Recommended Action: No patched version is available.
Plugin: Autocomplete Location field Contact Form 7
Vulnerability: Authenticated (Administrator+) Stored Cross-Site Scripting vulnerability
Patched Version: 3.0
Recommended Action: Update the WordPress Autocomplete Location field Contact Form 7 plugin to the latest available version (at least 3.0).
Plugin: WP Forms Puzzle Captcha
Vulnerability: CSRF to XSS vulnerability
Patched Version: None
Recommended Action: No patched version is available. No reply from the vendor.
Plugin: Super Progressive Web Apps
Vulnerability: Broken Access Control vulnerability
Patched Version: 2.2.22
Recommended Action: Update the WordPress Super Progressive Web Apps plugin to the latest available version (at least 2.2.22).
Plugin: WP Forms Puzzle Captcha
Vulnerability: Captcha Bypass vulnerability
Patched Version: None
Recommended Action: No patched version is available. No reply from the vendor.
Plugin: Widgets for Google Reviews
Vulnerability: Arbitrary File Upload vulnerability
Patched Version: 11.1
Recommended Action: Update the WordPress Widgets for Google Reviews plugin to the latest available version (at least 11.1).
Plugin: WCMultiShipping
Vulnerability: Broken Access Control vulnerability
Patched Version: 2.3.6
Recommended Action: Update the WordPress WCMultiShipping plugin to the latest available version (at least 2.3.6).
Plugin: Userpro
Vulnerability: Cross-Site Request Forgery via multiple functions vulnerability
Patched Version: 5.1.2
Recommended Action: Update the WordPress Userpro plugin to the latest available version (at least 5.1.2).